ESET Analysis
How ESET Analysis discovered a kill change that had been used to take down probably the most prolific botnets on the market
01 Nov 2023
•
,
3 min. learn

In August 2023, the infamous Mozi botnet, notorious for exploiting vulnerabilities in lots of of 1000’s of IoT units annually, skilled a sudden and unanticipated nosedive in exercise. First noticed in India on August 8th, 2023 and per week later in China on August 16th, this mysterious disappearance stripped Mozi bots of most of their performance.
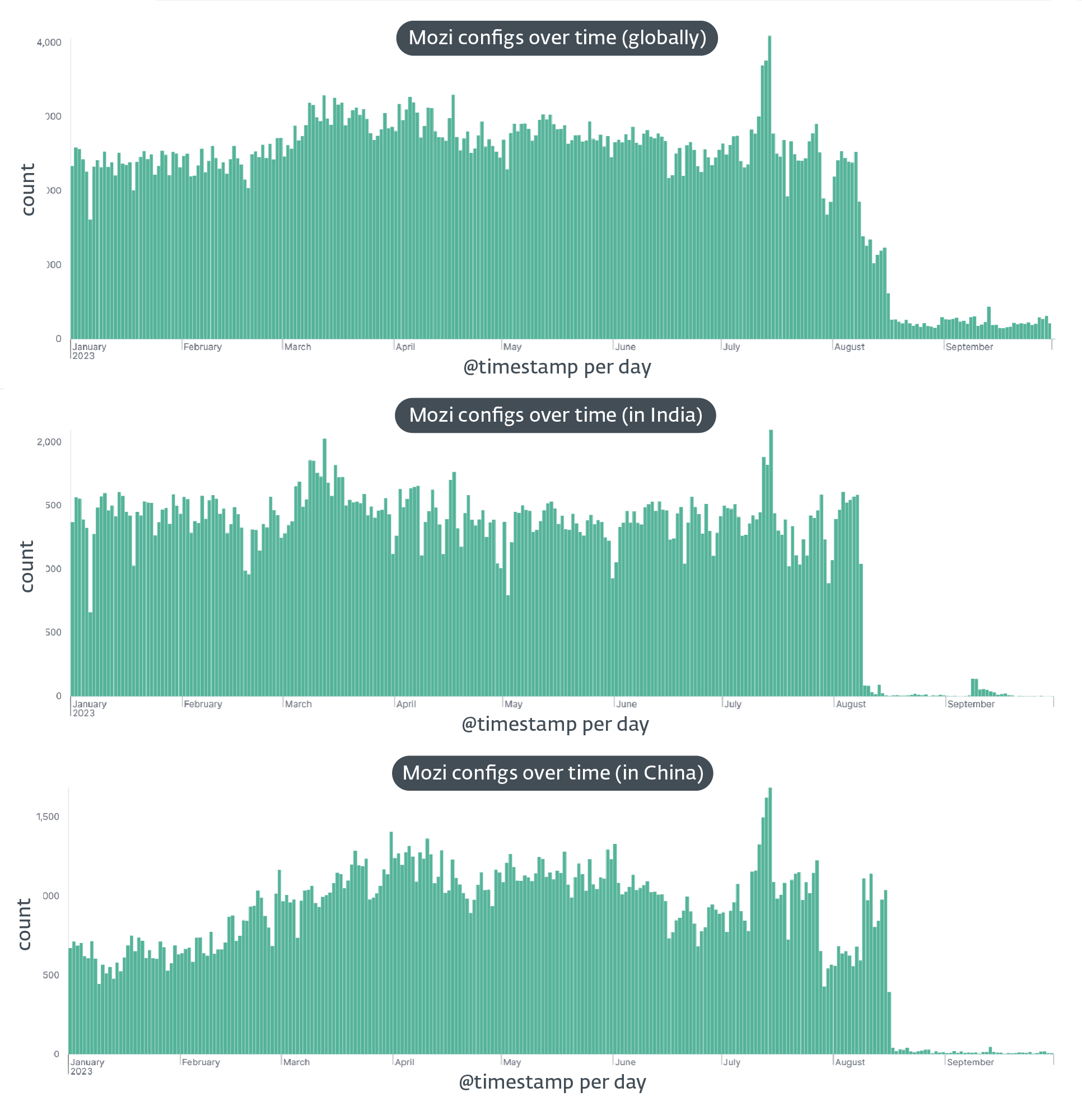
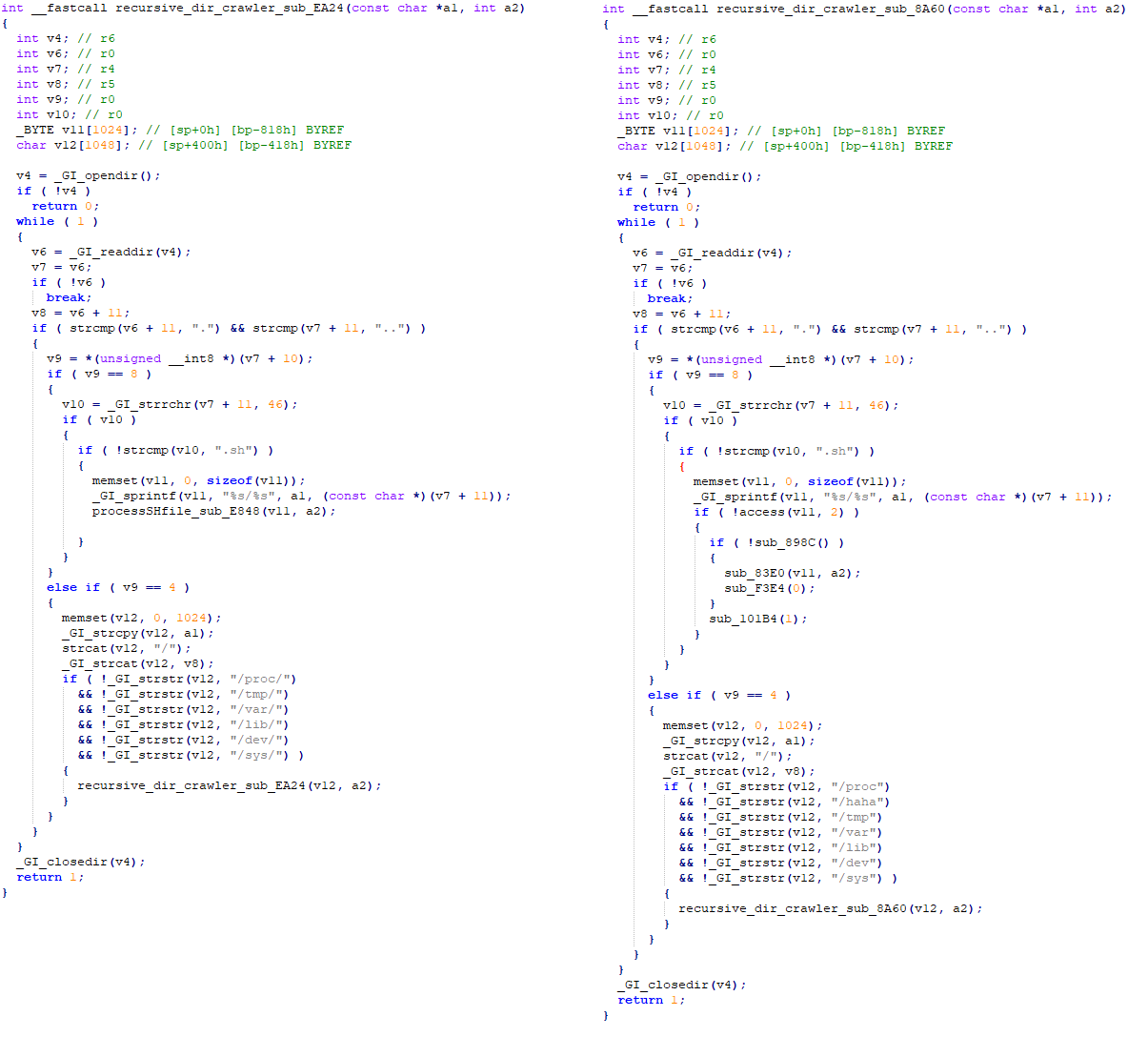
Our investigation into this occasion led us to the invention of a kill change on September 27th, 2023. We noticed the management payload (configuration file) inside a consumer datagram protocol (UDP) message that was lacking the everyday encapsulation of BitTorrent’s distributed sloppy hash desk (BT-DHT) protocol. The individual behind the takedown despatched the management payload eight occasions, every time instructing the bot to obtain and set up an replace of itself through HTTP.
The kill change demonstrated a number of functionalities, together with:
- killing the dad or mum course of, i.e., the unique Mozi malware,
- disabling some system companies equivalent to sshd and dropbear,
- changing the unique Mozi file with itself,
- executing some router/machine configuration instructions,
- disabling entry to numerous ports (iptables -j DROP), and
- establishing the identical foothold because the changed unique Mozi file
We recognized two variations of the management payload, with the newest one functioning as an envelope containing the primary one with minor modifications, equivalent to including a operate to ping a distant server, in all probability meant for statistical functions.
Regardless of the drastic discount in performance, Mozi bots have maintained persistence, indicating a deliberate and calculated takedown. Our evaluation of the kill change reveals a robust connection between the botnet’s unique supply code and just lately used binaries, and in addition using the right non-public keys to signal the management payload (see Determine 2).
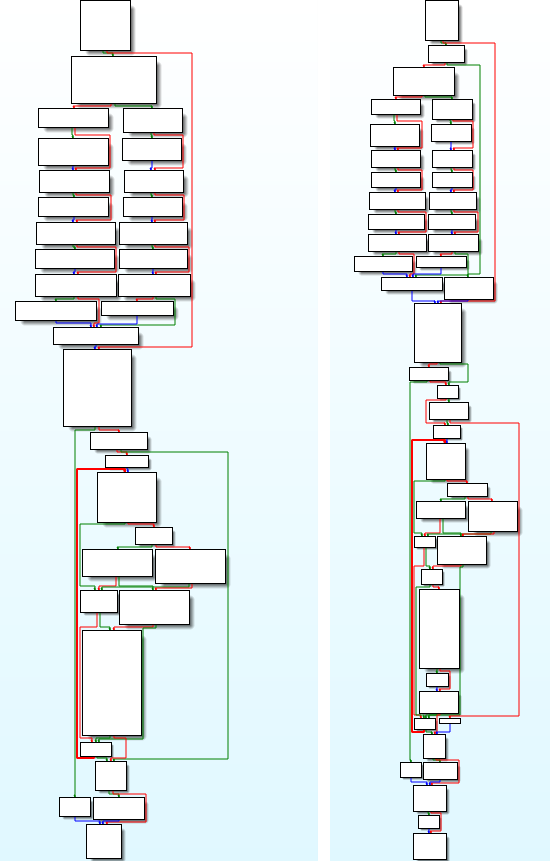
This leads us to the speculation suggesting two potential originators of this takedown: the Mozi botnet creators, or Chinese language legislation enforcement forcing the cooperation of the creators. The sequential focusing on of bots in India after which in China means that the takedown was carried out intentionally, with one nation focused first and the opposite per week later.
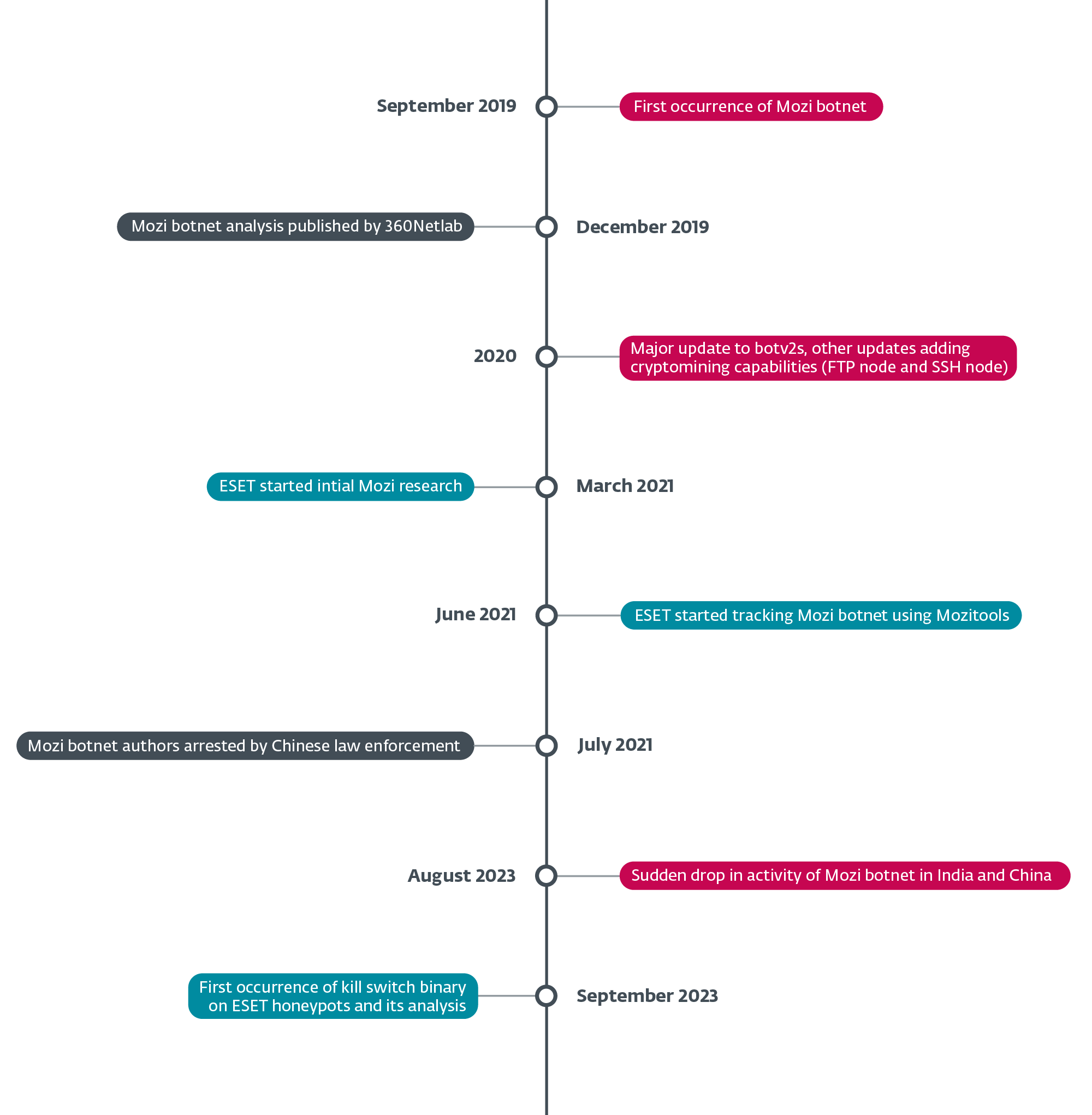
The demise of probably the most prolific IoT botnets is a captivating case of cyberforensics, offering us with intriguing technical data on how such botnets within the wild are created, operated, and dismantled. We’re persevering with to analyze this case and can publish an in depth evaluation within the coming months. However for now, the query stays: Who killed Mozi?
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides non-public APT intelligence reviews and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
758BA1AB22DD37F0F9D6FD09419BFEF44F810345 |
mozi.m |
Linux/Mozi.A |
Authentic Mozi bot. |
|
9DEF707F156DD4B0147FF3F5D1065AA7D9F058AA |
ud.7 |
Linux/Mozi.C |
Mozi bot kill change. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
157.119.75[.]16 |
N/A |
AS135373 EFLYPRO-AS-AP EFLY NETWORK LIMITED |
2023-09-20 |
Kill change internet hosting server |
MITRE ATT&CK strategies
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Useful resource Growth |
Purchase Infrastructure: Digital Personal Server |
The Mozi kill change operators rented a server at eflycloud.com to host the replace recordsdata. The Mozi kill change operators rented a number of servers that ship payloads on BT-DHT networks. |
|
|
Preliminary Entry |
Exploit Public-Dealing with Software |
The Mozi kill change operators despatched an replace command to Mozi purchasers on a BT-DHT community. |
|
|
Persistence |
Boot or Logon Initialization Scripts: RC Scripts |
The kill change creates a number of scripts, equivalent to /and so on/rc.d/rc.native, to determine persistence. |
|
|
Exfiltration |
Exfiltration Over Various Protocol: Exfiltration Over Unencrypted Non-C2 Protocol |
The kill change sends an ICMP ping to the operator maybe for the aim of monitoring. |
|
|
Impression |
Service Cease |
The kill change stops the SSH service and blocks entry to it with iptables. |

