Whereas supposed for comfort and environment friendly communication, electronic mail auto-forwarding guidelines can inadvertently result in the unauthorized dissemination of delicate info to exterior entities, placing confidential information vulnerable to publicity to unauthorized events. Wing Safety (Wing), a SaaS safety firm, introduced yesterday that their SaaS shadow IT discovery strategies now embody an answer that solves for auto-email forwarding as effectively. Whereas Wing’s shadow IT resolution is provided as a free device that may be onboarded and used as a self-service, customers prepared to improve will be capable to benefit from the firm’s new Gmail and Outlook integrations, which broaden the corporate’s discovery capabilities and prolong their information safety features.
The dangers of electronic mail auto-forwarding guidelines
Auto-forwarding emails is a good way to avoid wasting time on repetitive duties and are due to this fact highly regarded amongst workers who commonly collaborate and share info with exterior enterprise companions. Threat examples embody:
- Automation means nobody is checking for delicate or personal info. Emails with a sure phrase mixture within the title, or a selected sender, will routinely be forwarded to an exterior entity with none oversight. This could result in PII information leakage, delicate information leakage and regulatory violations that may compromise a company’s compliance.
- Auto-forwarding also can point out a possible insider danger. A disgruntled worker could auto-forward sure emails to rivals. It will also be as frequent as an worker who plans to go away the corporate and needs to keep up entry to their work after they go away – auto-forwarding emails to their personal electronic mail account.
- Malicious actors would possibly use this as an entry level. Unhealthy actors can use these electronic mail forwarding guidelines to exfiltrate information after a profitable assault, or as a way to unfold phishing campaigns inside organizations.
 |
| Screenshot from Wing’s platform, auto-forwarding points present in gmail and Outlook |
What’s the connection between SaaS Safety and electronic mail Safety?
For a number of causes, it’s important for organizations to uncover SaaS Shadow IT functions. Shadow IT refers back to the unauthorized use of IT methods inside a company, usually for the sake of comfort or effectivity, with out the specific approval of the IT division. There are some SaaS functions that will pose important dangers to the group’s safety, compliance, and total effectivity:
- Safety Dangers: SaaS functions are a part of the fashionable provide chain, and as such they need to endure correct vendor danger assessments and person entry evaluations previous to connecting them to firm information. With Shadow IT, breached functions, non-compliant functions or malicious functions go unnoticed.
- Compliance Issues: Many industries have strict regulatory necessities that should be adhered to, significantly regarding information privateness and safety. Utilizing unauthorized functions may end up in non-compliance, resulting in authorized penalties, fines, and harm to the group’s status.
- Monetary Implications: Uncontrolled proliferation of Shadow IT functions can result in pointless expenditure. Organizations would possibly find yourself paying for redundant providers or duplicate accounts, resulting in negligent spending and monetary waste.
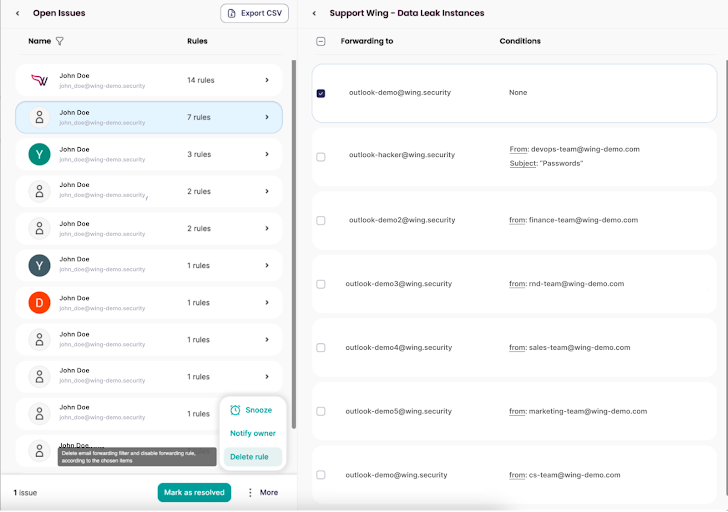 |
| Wing’s product illustration – dangerous electronic mail forwarding guidelines |
Wing’s SaaS discovery entails the systematic identification, categorization, and evaluation of a company’s SaaS utilization to mitigate shadow IT dangers. The corporate gives three distinct and non-intrusive discovery strategies: Connecting to organizations’ main SaaS functions (e.g., Google Drive, Salesforce, Slack, and others) to establish related functions, scanning endpoints for SaaS signature hits and cross-checking them with Wing’s intensive SaaS database of over 280,000 SaaS data. Their third and newly launched functionality includes connecting to enterprise emails and conducting scans to detect clear indications of SaaS utilization. Wing emphasizes that figuring out is simply step one in fixing and due to this fact gives clients the means to remediate and get rid of dangerous shares instantly inside their platform.