Cybersecurity researchers have developed what is the first totally undetectable cloud-based cryptocurrency miner leveraging the Microsoft Azure Automation service with out racking up any expenses.
Cybersecurity firm SafeBreach stated it found three completely different strategies to run the miner, together with one that may be executed on a sufferer’s setting with out attracting any consideration.
“Whereas this analysis is important due to its potential influence on cryptocurrency mining, we additionally consider it has severe implications for different areas, because the strategies could possibly be used to attain any job that requires code execution on Azure,” safety researcher Ariel Gamrian stated in a report shared with The Hacker Information.
The research primarily got down to establish an “final crypto miner” that provides limitless entry to computational sources, whereas concurrently requiring little-to-no upkeep, is cost-free, and undetectable.
That is the place Azure Automation is available in. Developed by Microsoft, it is a cloud-based automation service that permits customers to automate the creation, deployment, monitoring, and upkeep of sources in Azure.
SafeBreach stated it discovered a bug within the Azure pricing calculator that made it potential to execute an infinite variety of jobs completely freed from cost, though it pertains to the attacker’s setting itself. Microsoft has since issued a repair for the issue.
Another technique entails making a test-job for mining, adopted by setting its standing as “Failed,” after which creating one other dummy test-job by benefiting from the truth that just one check can run on the identical time.
The top results of this stream is that it utterly hides code execution throughout the Azure setting.
A risk actor might leverage these strategies by establishing a reverse shell in the direction of an exterior server and authenticating to the Automation endpoint to attain their targets.
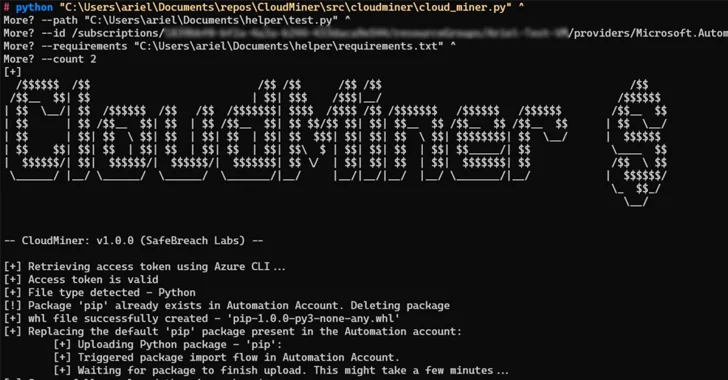
Moreover, it was discovered that code execution could possibly be achieved by leveraging Azure Automation’s function that permits customers to add customized Python packages.
“We might create a malicious package deal named ‘pip’ and add it to the Automation Account,” Gamrian defined.
“The add stream would exchange the present pip within the Automation account. After our customized pip was saved within the Automation account, the service used it each time a package deal was uploaded.”
SafeBreach has additionally made out there a proof-of-concept dubbed CoinMiner that is designed to get free computing energy inside Azure Automation service by utilizing the Python package deal add mechanism.
Microsoft, in response to the disclosures, has characterised the conduct as “by design,” which means the strategy can nonetheless be exploited with out getting charged.
Whereas the scope of the analysis is proscribed to the abuse of Azure Automation for cryptocurrency mining, the cybersecurity agency warned that the identical strategies could possibly be repurposed by risk actors to attain any job that requires code execution on Azure.
“As cloud supplier clients, particular person organizations should proactively monitor each single useful resource and each motion being carried out inside their setting,” Gamrian stated.
“We extremely advocate that organizations educate themselves in regards to the strategies and flows malicious actors might use to create undetectable sources and proactively monitor for code execution indicative of such conduct.”