
A brand new macOS malware dubbed ‘KandyKorn’ has been noticed in a marketing campaign attributed to the North Korean Lazarus hacking group, focusing on blockchain engineers of a cryptocurrency change platform.
The attackers impersonate members of the cryptocurrency neighborhood on Discord channels to unfold Python-based modules that set off a multi-stage KandyKorn an infection chain.
Elastic Safety found and attributed the assaults to Lazarus primarily based on overlaps with previous campaigns in regards to the employed methods, community infrastructure, code-signing certificates, and customized Lazarus detection guidelines.
Concentrating on the crypto neighborhood
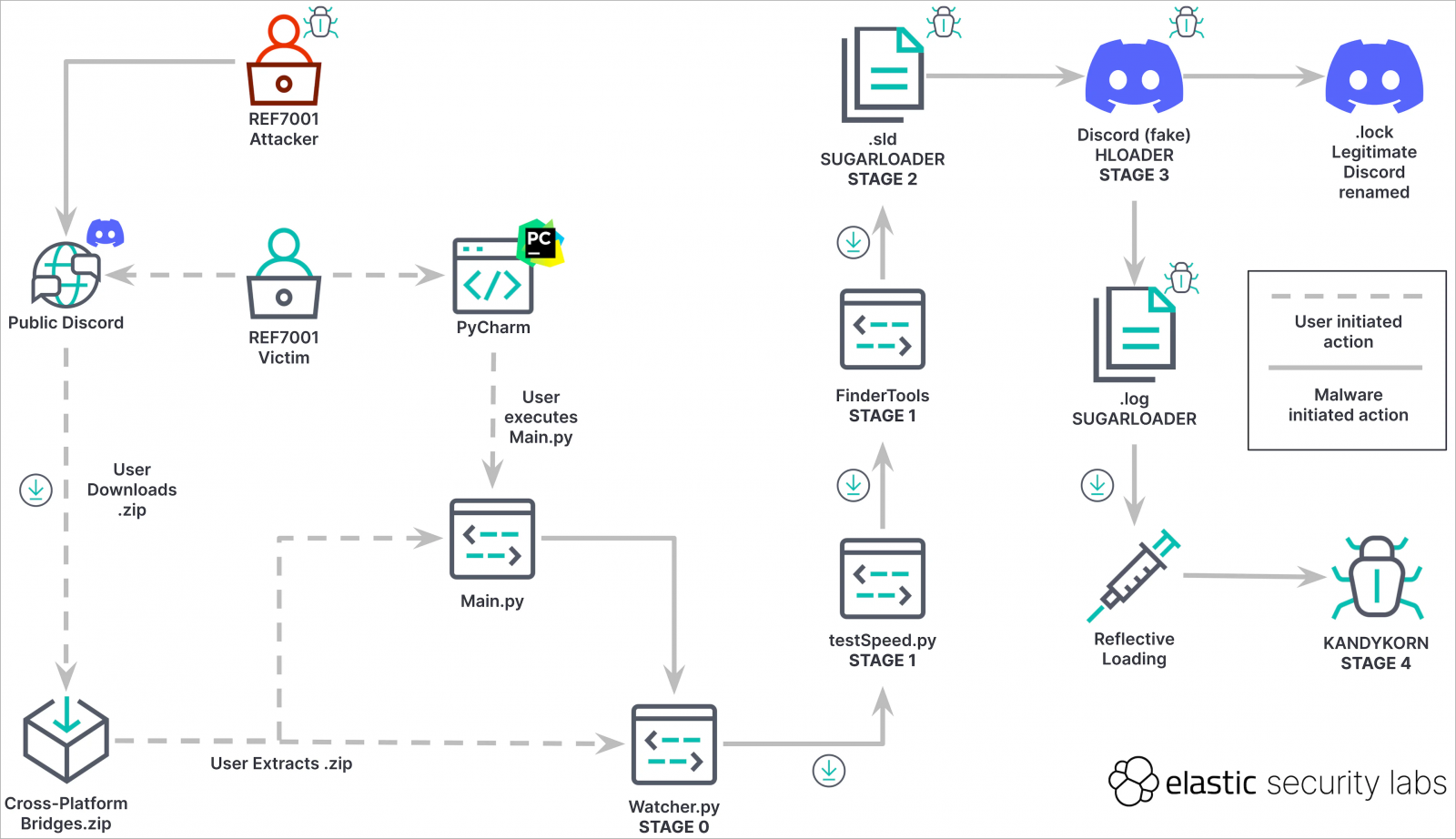
The assault, which begins on Discord, begins with social engineering assaults on targets to trick them into downloading a malicious ZIP archive named ‘Cross-platform Bridges.zip.’
The sufferer is misled into believing they’re downloading a reliable arbitrage bot designed for automated revenue era from cryptocurrency transactions.
As an alternative, the contained Python script (‘Important.py’) will import 13 modules from an equal variety of scripts within the ZIP, launching the primary payload, ‘Watcher.py.’
Watcher.py is a downloader that unpacks and executes a second Python script named ‘testSpeed.py’ together with one other Python file named ‘FinderTools,’ downloaded from a Google Drive URL.
FinderTools is a dropper that fetches and launches an obfuscated binary named ‘SugarLoader,’ which seems beneath two names and cases, as an .sld and a .log Mach-O executables.
Sugarloader establishes a reference to the command and management (C2) server to get and cargo the ultimate payload, KandyKorn, into reminiscence utilizing reflective binary loading.
macOS persistence trick
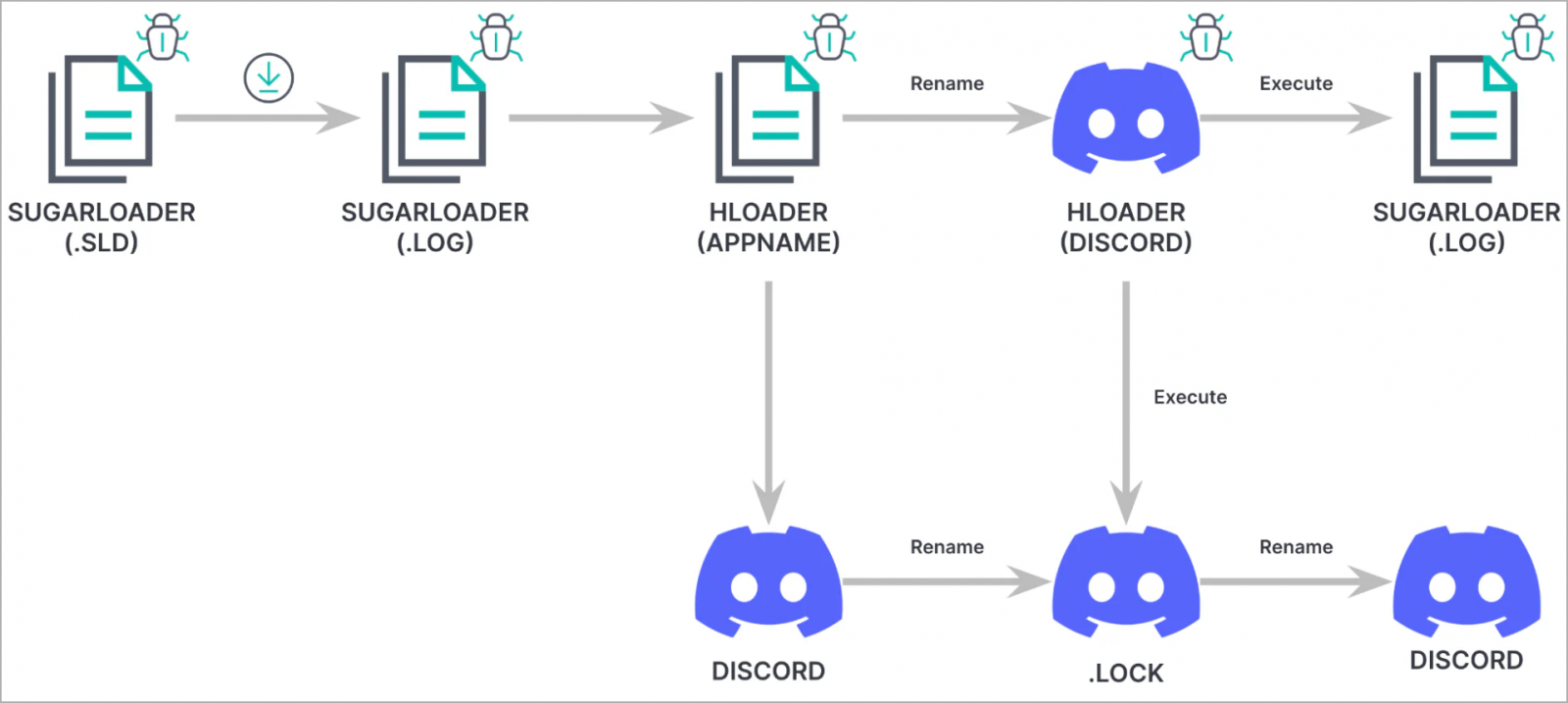
On the ultimate stage of the assault, a loader often known as HLoader is used, which impersonates Discord and makes use of macOS binary code-signing methods seen in previous Lazarus campaigns.
HLoader establishes persistence for SugarLoader by hijacking the true Discord app on the contaminated system, following a sequence of binary renaming actions.
“We noticed the risk actor adopting a way we’ve got not beforehand seen them use to realize persistence on macOS, often known as execution movement hijacking,” explains Elastic.
Particularly, HLOADER performs the next operations upon launch:
- Renames itself from Discord to MacOS.tmp
- Renames the reliable Discord binary from .lock to Discord
- Executes each Discord and .log utilizing NSTask.launchAndReturnError
- Renames each recordsdata again to their preliminary names
KandyKorn
KandyKorn is a sophisticated final-stage payload that permits Lazarus to entry and steal knowledge from the contaminated laptop.
It operates within the background as a daemon, ready for instructions from the C2 server and avoiding sending heartbeats to attenuate its hint on the system.
KandyKorn helps the next 16 instructions:
- 0xD1: Terminates this system.
- 0xD2: Gathers system information.
- 0xD3: Lists listing contents.
- 0xD4: Analyzes listing properties.
- 0xD5: Uploads recordsdata from the C2 to the sufferer’s laptop.
- 0xD6: Exfiltrate recordsdata from the sufferer to the C2.
- 0xD7: Archives and exfiltrates directories.
- 0xD8: Securely deletes recordsdata utilizing overwriting with zeros.
- 0xD9: Lists all working processes.
- 0xDA: Kills a specified course of.
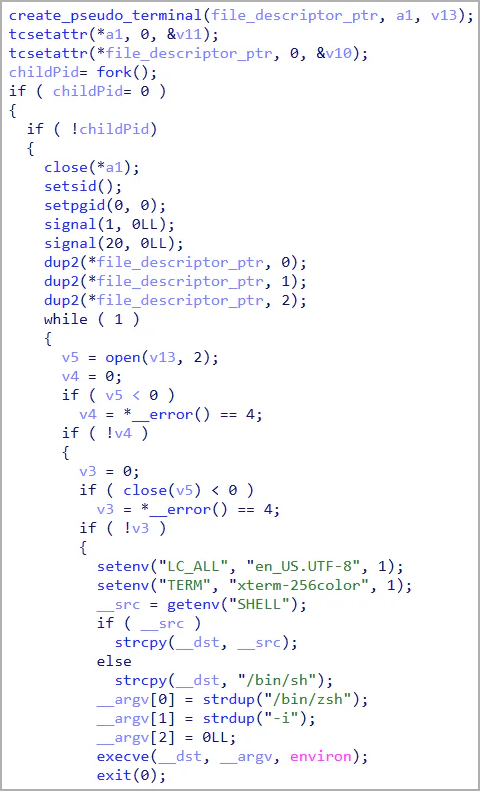
- 0xDB: Executes system instructions by way of a pseudoterminal.
- 0xDC: Retrieves command outputs.
- 0xDD: Initiates an interactive shell.
- 0xDE: Retrieves present configuration.
- 0xDF: Updates C2 configuration.
- 0xE0: Pauses operations quickly.
In abstract, KandyKorn is a very stealthy backdoor able to knowledge retrieval, listing itemizing, file add/obtain, safe deletion, course of termination, and command execution.
The cryptocurrency sector stays a major goal for Lazarus, primarily motivated by monetary achieve relatively than espionage, which is their different principal operational focus.
The existence of KandyKorn underscores that macOS is effectively inside Lazarus’ focusing on vary, showcasing the risk group’s exceptional potential to craft subtle and inconspicuous malware tailor-made for Apple computer systems.
