The surprising drop in malicious exercise related with the Mozi botnet in August 2023 was as a result of a kill change that was distributed to the bots.
“First, the drop manifested in India on August 8,” ESET mentioned in an evaluation printed this week. “Per week later, on August 16, the identical factor occurred in China. Whereas the mysterious management payload – aka kill change – stripped Mozi bots of most performance, they maintained persistence.”
Mozi is an Web of Issues (IoT) botnet that emerged from the supply code of a number of recognized malware households, akin to Gafgyt, Mirai, and IoT Reaper. First noticed in 2019, it is recognized to take advantage of weak and default distant entry passwords in addition to unpatched safety vulnerabilities for preliminary entry.
In September 2021, researchers from cybersecurity agency Netlab disclosed the arrest of the botnet operators by Chinese language authorities.
However the precipitous decline in Mozi exercise – from round 13,300 hosts on August 7 to three,500 on August 10 – is claimed to be the results of an unknown actor transmitting a command instructing the bots to obtain and set up an replace designed to neutralize the malware.
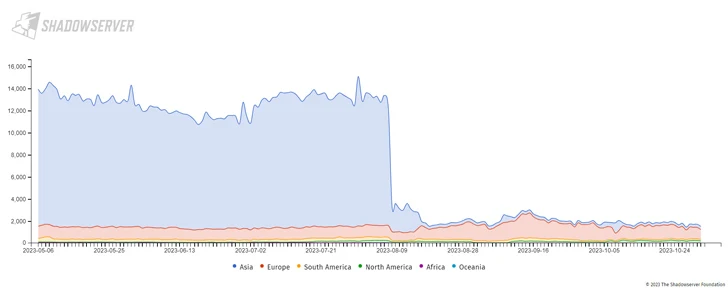 |
| Shadowserver Basis |
Particularly, the kill change demonstrated capabilities to terminate the malware’s course of, disable system providers akin to SSHD and Dropbear, and in the end change Mozi with itself.
“Regardless of the drastic discount in performance, Mozi bots have maintained persistence, indicating a deliberate and calculated takedown,” safety researchers Ivan Bešina, Michal Škuta, and Miloš Čermák mentioned.
A second variant of the management payload got here fitted with minor modifications, together with a characteristic to ping a distant server, possible for statistical functions. What’s extra, the kill change reveals a robust overlap with the botnet’s unique supply code and is signed with the right non-public key beforehand utilized by the unique Mozi operators.
“There are two potential instigators for this takedown: the unique Mozi botnet creator or Chinese language regulation enforcement, maybe enlisting or forcing the cooperation of the unique actor or actors,” Bešina mentioned.
“The sequential concentrating on of India after which China means that the takedown was carried out intentionally, with one nation focused first and the opposite every week later.”



